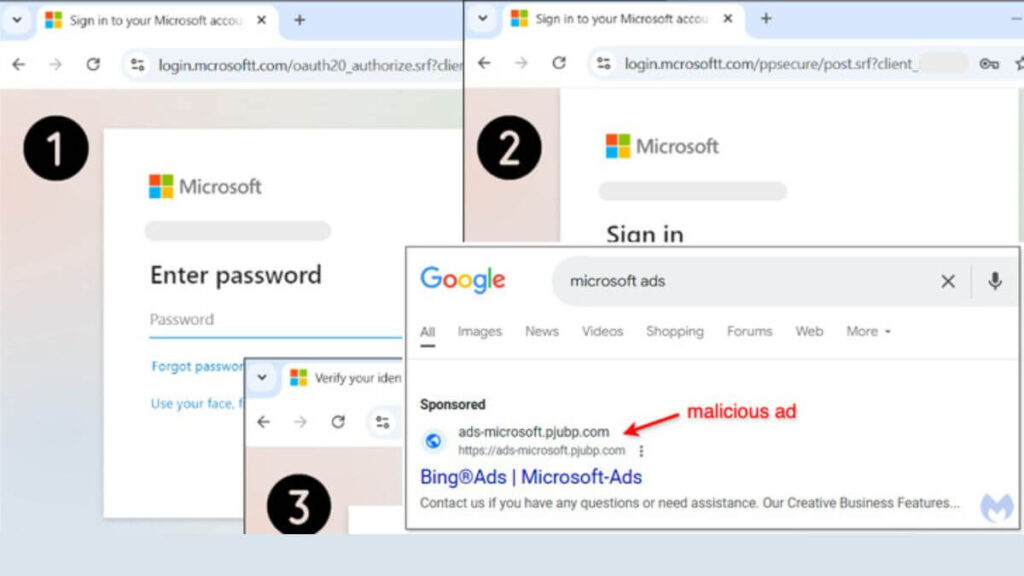
Cybercriminals are now using fake Google ads to steal Microsoft advertising accounts. They create phishing pages that look real to trick users. These scams can lead to financial losses and data breaches. Advertisers must stay alert and protect their credentials.
How the Malvertising Scam Works
Attackers use Google Search ads to target Microsoft advertisers. Users searching for “Microsoft Ads” see fake sponsored ads. Clicking on these ads leads to phishing pages that steal login details. These pages look just like the real Microsoft Ads login page.
The attackers use several tricks to avoid detection. If someone accesses the fake site from a VPN, they are redirected to a harmless marketing page. Security tools often fail to detect these tactics.
Another interesting trick is how they handle direct visits. If someone manually enters the phishing site URL, they are redirected to a random YouTube video. This helps attackers avoid detection by security teams.
Why This Attack is Dangerous
This scam is very dangerous for businesses. It can result in:
- Stolen login credentials and two-factor authentication (2FA) codes.
- Unauthorized access to advertising accounts.
- Misuse of advertising budgets for malicious campaigns.
- Loss of sensitive business data.
The phishing pages capture login details and send them to attackers. Once they gain access, they can run fraudulent ad campaigns. This can drain company budgets and damage reputations.
Also read | Malvertising Attack Hijacks Google Ads Users Steals Credentials
Attackers Targeting Other Platforms
This is not the first time cybercriminals have used fake Google ads. A similar attack targeted Google Ads users. The attackers used fake domains ending in “.pt” (Portugal). Now, Microsoft’s advertising platform users are being targeted using “.com.br” (Brazil).
Cybersecurity researchers found phishing domains linked to Brazil. This suggests a large-scale operation targeting multiple advertising platforms. Even Meta (Facebook) advertising accounts could be at risk.
How Google is Responding
Google claims to take strict action against such scams. They say they remove fraudulent ads when detected. However, attackers keep finding new ways to bypass security checks.
Google encourages users to report suspicious ads. But the speed of response is often slow, allowing scams to spread.
Who is Behind These Attacks?
A Chinese-speaking group called Smishing Triad is suspected in the USPS scam. They have targeted postal services in over 100 countries. Their phishing-as-a-service (PhaaS) toolkit, called Darcula, is widely used.
Researchers believe these scammers are skilled in bypassing security tools. This explains why their campaigns are so successful.
Also read | Fake CAPTCHA Spreads Lumma Stealer in Multi-Industry Attacks
Smishing Attacks Target USPS Users
Along with fake ads, attackers are also using SMS phishing (smishing). They pretend to be from the United States Postal Service (USPS). They send messages about fake failed deliveries.
Victims receive an SMS asking them to update their address using a PDF file. Clicking the link leads to a fake USPS website. Here, users are asked to enter personal details, including payment information.
Researchers found that attackers use advanced techniques to avoid detection. The phishing pages even ask for credit card details, claiming a redelivery fee.
Also read | DeepSeek Security Breach Exposes 1 Million Log Lines and Secret Keys
Why Mobile Users are at Risk
Mobile users are easier targets for phishing scams. Many security tools work better on computers than on smartphones. Cybercriminals take advantage of this gap to trick mobile users.
They use special methods to bypass security checks. For example, iMessage normally blocks suspicious links. But attackers include text like “Reply Y to continue” to disable this protection.
How to Protect Yourself from Malvertising and Phishing Attacks
Online advertisers and mobile users should take steps to stay safe.
- Verify URLs Before Clicking
Always check website addresses before entering login details. Scammers often use domains that look real but have small changes. - Enable Multi-Factor Authentication (MFA)
Use MFA to protect accounts. Even if attackers steal your password, they may not be able to access your account. - Avoid Clicking on Suspicious Ads
Do not trust sponsored ads, even on Google. Instead, type the official website address manually in your browser. - Use Security Tools
Install browser security extensions that warn you about phishing sites. Keep your security software updated. - Stay Alert for Fake SMS Messages
Do not click on links in text messages claiming failed deliveries. Visit the official website instead. - Report Suspicious Ads and Messages
If you see a suspicious ad, report it to Google. If you receive a phishing SMS, report it to your service provider.
Conclusion
Cybercriminals are getting smarter, using fake Google ads and phishing messages to steal sensitive data. Microsoft advertisers and mobile users must stay cautious. Always verify website links, enable extra security layers, and report suspicious activity. Staying informed is the best way to stay protected.