A new security exploit, Double Clickjacking, has emerged as a significant threat to websites. This technique bypasses existing security measures, making user accounts vulnerable. Paulos Yibelo, a security researcher, discovered this exploit, which uses a double-click sequence to manipulate user actions online.
What is Double Clickjacking?
DoubleClickjacking is a variation of the clickjacking attack. Clickjacking tricks users into clicking on hidden or malicious elements on a webpage. DoubleClickjacking adds a twist by exploiting the timing between two clicks. This method allows attackers to bypass protections like X-Frame-Options and SameSite cookies.
The exploit targets the brief moment between the first and second clicks. During this time, attackers redirect users to malicious pages or execute harmful actions.
What is a Clickjacking Attack?
Clickjacking, also called UI redressing, is a cyberattack where users are tricked into clicking hidden elements on a webpage. These clicks perform unintended actions, such as sharing sensitive data, approving permissions, or downloading malware.
Hackers overlay malicious content on a legitimate-looking interface. Users believe they are interacting with a safe webpage, but their actions trigger harmful operations.
How Double Clickjacking Works?
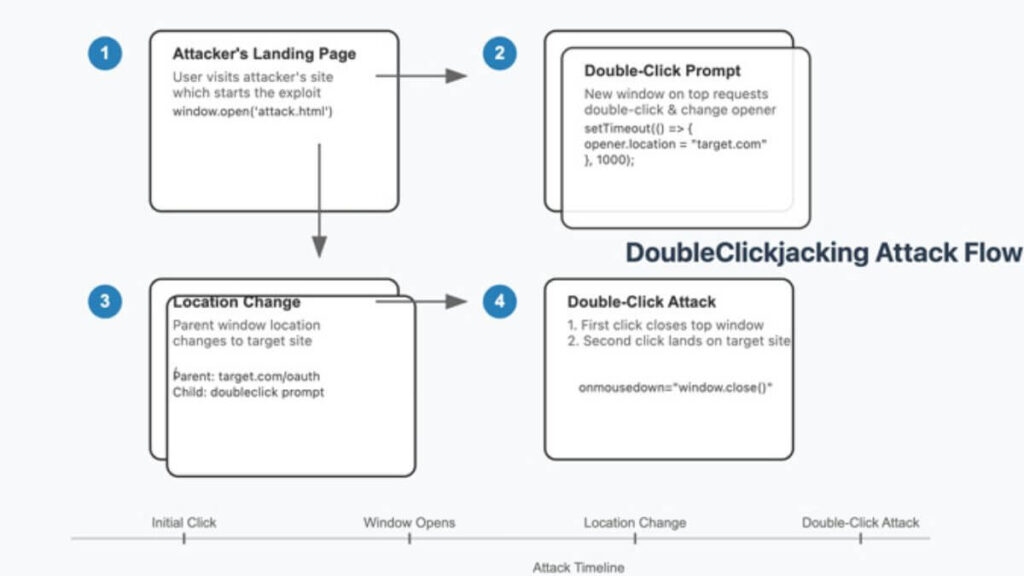
DoubleClickjacking follows a simple but effective process. An attacker creates a website designed to lure users. This site opens a new browser window or tab when users interact with it. The new window mimics legitimate actions like CAPTCHA verification. It prompts users to double-click to proceed.
During the second click, attackers redirect the page using JavaScript to a malicious site. This site might authorize harmful actions, like approving access for a malicious application. Users unknowingly complete actions they never intended.
DoubleClickjacking follows a systematic approach:
- Website Manipulation: The attacker creates a site designed to lure users. This site opens a new browser window when clicked.
- Double-Click Prompt: The new window mimics legitimate elements like CAPTCHA verification. It asks users to double-click to proceed.
- Exploitation: During the second click, the attacker redirects the page to a malicious site using JavaScript.
- Account Takeover: The malicious site tricks users into approving sensitive actions, such as authorizing malicious applications.
These steps allow attackers to steal data or take over accounts with minimal user interaction.
Why is Double Clickjacking Dangerous?
DoubleClickjacking is dangerous because it bypasses all known clickjacking defenses. Traditional protections assume a single click as the attack vector. They do not account for the manipulation of double-click sequences.
Methods like X-Frame-Options, SameSite cookies, or Content Security Policies cannot prevent this exploit. This makes DoubleClickjacking a serious threat to websites and their users. Security frameworks assume single-click attacks, leaving them vulnerable to this advanced method.
Also read | Critical security flaws fixed in Microsoft Dynamics 365 and Power Apps Web API
Examples of DoubleClickjacking Exploits
Paulos Yibelo demonstrated how DoubleClickjacking could exploit websites like Coinbase and Yahoo. Attackers could use OAuth applications with predictable values to hijack user accounts. Logged-in users visiting malicious sites could unknowingly authorize harmful actions.
- OAuth Exploits: Attackers use predictable values in authorization requests to hijack accounts.
- Cross-Site Manipulation: Users logged into sites like Yahoo! or Coinbase can unknowingly authorize malicious applications.
Affected Platforms
Platforms like Salesforce, Slack, and Shopify have been identified as vulnerable to this attack. Additionally, browser extensions such as crypto wallets and VPNs are susceptible, enabling attackers to authorize fraudulent transactions or disable security features.
Key Risks
- Account Takeovers: Attackers can gain unauthorized access to user accounts.
- Malicious App Authorization: Permissions are granted to harmful applications, exposing sensitive user data.
- Critical Account Changes: Attackers may modify settings, disable security features, or initiate financial transactions.
Bypassing Existing Protections
Traditional safeguards like Content Security Policies (CSP), SameSite cookies, and X-Frame-Options headers are ineffective against DoubleClickjacking.
Also read | Top 10 Cybersecurity trends to expect in 2025
How Can Websites Prevent DoubleClickjacking?
Website owners can mitigate this threat using client-side solutions. Here are some effective measures:
- Disable Buttons by Default: Disable critical buttons until users perform mouse gestures or key presses.
- Use Advanced Event Detection: Monitor unusual timing between user clicks to detect suspicious activity.
- Adopt New Standards: Browser vendors should implement protections similar to X-Frame-Options for double-click vulnerabilities.
Client-Side Protections
Web developers can implement JavaScript-based solutions to prevent unauthorized clicks on sensitive elements. Here’s a sample javascript code:
(function () {
if (window.matchMedia && window.matchMedia("(hover: hover)").matches) {
var buttons = document.querySelectorAll('form button, form input[type="submit"]');
buttons.forEach(button => button.disabled = true);
function enableButtons() {
buttons.forEach(button => button.disabled = false);
}
document.addEventListener("mousemove", enableButtons);
document.addEventListener("keydown", e => {
if (e.key === "Tab") enableButtons();
});
}
})();This code ensures buttons remain disabled until user activity like mouse movement or key presses is detected.
Long-Term Browser Solutions
Advocating for browser-level changes is essential for systemic protection. Possible measures include:
- A Double-Click-Protection HTTP Header to regulate multi-click interactions.
- Enhancements to CSP directives to account for context-switching in multi-click scenarios.
Developer Best Practices
- Protect sensitive pages with additional scripts and authentication checks.
- Limit the use of
window.openerto prevent unauthorized navigation changes. - Implement stricter controls over embedded content in iframes.
Some websites, like Dropbox, already use such methods to secure their platforms. Browser vendors should also introduce new standards to defend against double-click exploits.
Also read | 5 Practical techniques for effective cyber threat hunting
Long-Term Solutions
Long-term solutions require collaboration between website developers and browser vendors. Developers must adopt client-side protections to detect and block suspicious actions. Browsers should introduce enhanced security headers to address timing-based vulnerabilities.
Conclusion
DoubleClickjacking reveals a new layer of vulnerabilities in web security. It exploits double-click timing to bypass protections and compromise accounts. Website owners must adopt proactive measures to secure their platforms. Early detection and prevention can secure user data and prevent account takeovers.
FAQs
1. What is DoubleClickjacking?
DoubleClickjacking is a cyberattack that manipulates user interactions through a two-click sequence to bypass existing protections and execute unauthorized actions.
2. Why is DoubleClickjacking dangerous?
The attack’s minimal interaction requirements and ability to bypass traditional defenses make it a significant threat to websites and user accounts.
3. How can developers prevent DoubleClickjacking?
Developers can use JavaScript-based client-side protections, enhance sensitive pages, and advocate for browser-level security updates.
4. Which platforms are vulnerable to DoubleClickjacking?
Platforms using OAuth for account authorization, including Salesforce, Slack, and Shopify, are particularly at risk.
5. Can browser updates mitigate this attack?
Yes, introducing Double-Click-Protection HTTP headers and updating CSP directives can help prevent these attacks.