Session hijacking is becoming a preferred method for bypassing multi-factor authentication (MFA). Attackers are using new techniques to exploit user sessions, making this an alarming trend in cybersecurity. Microsoft reports that over 147,000 token replay attacks occurred in 2023 alone. This represents a massive 111% increase from the previous year.
But what’s causing this rise in session hijacking? Let’s explore.
How Session Hijacking Has Changed
Session hijacking is not a new attack method. It has existed for years. In the past, hackers relied on man-in-the-middle (MitM) attacks to steal session data by snooping on unsecured networks. They also used cross-site scripting (XSS) to steal user sessions.
Session hijacking no longer focuses on local network traffic. Instead, modern attacks happen over the public internet, targeting cloud-based applications. Attackers steal valid session data like cookies, tokens, and IDs to gain unauthorized access to apps. These stolen sessions let them bypass MFA and other security controls.
Why Attackers Steal Sessions
Attackers prefer stealing live sessions because it helps them avoid the hassle of cracking passwords or defeating MFA. Once they get hold of session data, they can take over user accounts without re-authenticating.
Session tokens, in theory, expire quickly. But, in reality, they can last for days or even months if the session remains active. This extended validity makes it more dangerous.
When attackers steal sessions, they gain access to multiple apps and sensitive data. If attackers break into an identity provider (IDP) like Okta or Microsoft Entra, they can access all apps connected to that account.
Comparing Different Session Hijacking Methods
There are two common methods attackers use for session hijacking today: phishing toolkits and infostealers. Both methods can target credentials and session cookies. Let’s break them down:
1. Phishing Attacks: AitM and BitM
Attackers use phishing tools like Adversary-in-the-Middle (AitM) and Browser-in-the-Middle (BitM) to trick users into giving away session data. In AitM, the attacker intercepts authentication materials, including session tokens. BitM is even more dangerous, as it allows attackers to remotely control the victim’s browser and steal session tokens.
2. Infostealers
Infostealers are malware programs that harvest session cookies and other sensitive data from users’ browsers. Infected websites, malicious ads, or even social media can deliver them. Unlike AitM, infostealers are less targeted and more compromising a broader range of sessions.
Infostealers are flexible. If one app blocks the attacker, they can try to exploit another app. This makes them a dangerous tool in session hijacking.
Are Infostealers Blocked by EDR?
Endpoint Detection and Response (EDR) tools may block common infostealers, but it’s not a guarantee. Sophisticated attackers often use custom malware that evades detection. Even with EDR in place, attackers can still compromise personal devices, especially in Bring Your Device (BYOD) environments.
Once an attacker gets hold of session data from a compromised device, they can move to corporate accounts. EDR isn’t foolproof when it comes to preventing session hijacking through infostealers.
What About Passkeys?
Passkeys are a secure authentication method designed to prevent phishing attacks like AitM and BitM. However, passkeys are not effective against infostealers. Infostealers don’t rely on authentication; they resume an already active session, bypassing passkey security.
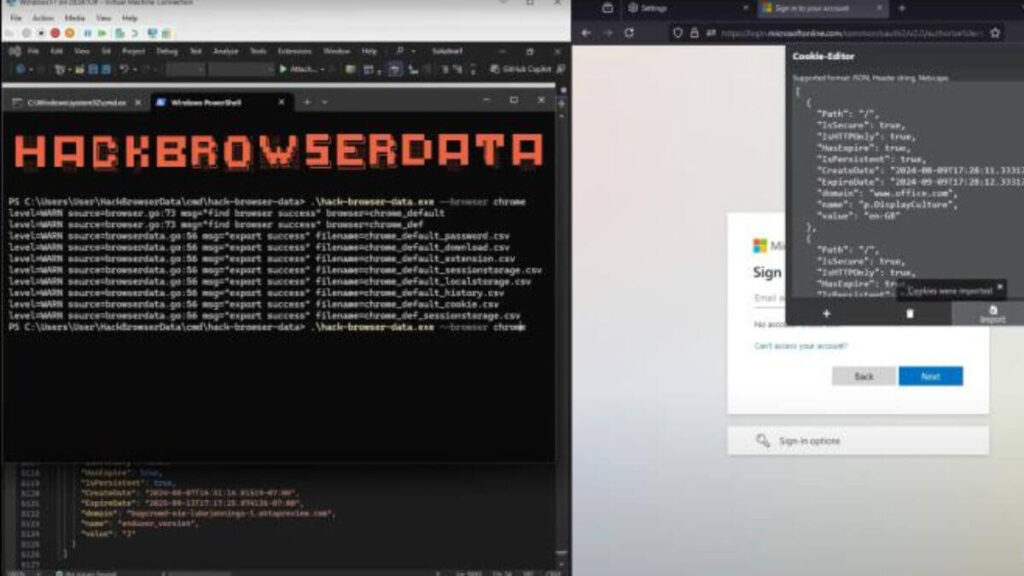
Demo: Session hijacking using stolen cookies
How to Detect and Respond to Session Hijacking
There are several ways to prevent session hijacking. First, security teams need to detect unauthorized sessions. App-level controls can help block suspicious activity, but these are not always foolproof. While some apps may enforce IP restrictions, attackers often find ways around them using proxy networks.
A new defense strategy involves browser-based detection. Companies can track when and where a session is used by injecting a marker into the browser’s session. If someone uses the session in an unexpected location or browser, it indicates a possible hijacking attempt.
Conclusion
Session hijacking is a growing threat that can bypass even advanced security measures like MFA. Attackers are constantly innovating their techniques, and traditional defenses are no longer enough.