A dangerous Android malware named DroidBot targets banks, cryptocurrency exchanges, and national organizations. This remote access trojan (RAT) malware uses advanced techniques to attack its victims. It combines hidden VNC, overlay attacks, and spyware-like capabilities such as keylogging and monitoring user interfaces.
Cleafy researchers Simone Mattia, Alessandro Strino, and Federico Valentini discovered this malware. They report that DroidBot uses dual-channel communication for greater flexibility and resilience. The malware transmits data using MQTT and receives commands through HTTPS.
DroidBot’s Malware-as-a-Service (MaaS) model allows affiliates to use its capabilities for a monthly fee of $3,000. It has impacted at least 77 financial institutions and organizations across Europe and beyond.
What is DroidBot?
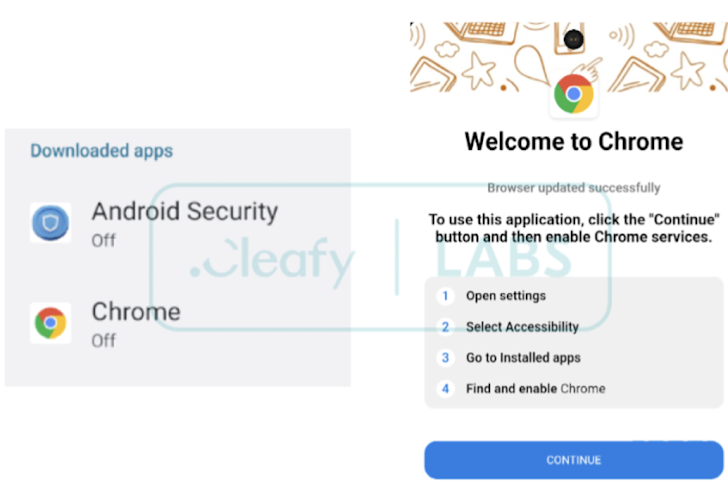
DroidBot is a modern Android malware designed to attack financial systems. It allows hackers to control infected devices remotely. The malware disguises itself as legitimate apps like banking apps, Google Chrome, or generic security applications. Its primary goal is to steal sensitive information and compromise systems.
Cleafy researchers revealed that DroidBot has been active since June 2024. It became widely known after its discovery in late October 2024. This RAT is sold as a service, enabling affiliates to use it for customized attacks.
How DroidBot Operates
DroidBot works by exploiting Android’s accessibility services. These services allow it to monitor device activity, record keystrokes, and take control. It also uses two different communication protocols to operate efficiently.
The malware uses HTTPS to receive commands from hackers and MQTT to send stolen data back. MQTT is a messaging protocol often used in IoT devices, making DroidBot more versatile and resilient.
This dual-channel approach separates inbound and outbound communication. It ensures better control and reduces the chances of detection.
Also read | Google’s New Restore Credentials Tool Simplifies App Login
The Business Model
It operates under a malware-as-a-service (MaaS) model. Affiliates pay $3,000 monthly to access this malware. This fee provides access to:
- A web control panel for customization.
- Tools to generate infected APK files.
- Options to issue commands and control infected devices.
At least 17 affiliate groups are currently using DroidBot. They customize the malware to target specific victims and steal sensitive data.
Affected Countries
DroidBot has been detected in several countries, including Austria, Belgium, France, Italy, Portugal, Spain, Turkey, and the United Kingdom. These campaigns are widespread and focus on financial systems and individual users.
The apps carrying DroidBot appear legitimate, making it harder for users to identify the threat.
Why it is Dangerous
It is not technically advanced compared to other malware, but its operational model is unique. The MaaS scheme gives affiliates powerful tools for creating custom attacks.
Its use of Android accessibility services makes it capable of stealing data and controlling devices remotely. Leveraging MQTT and HTTPS protocols ensures flexibility and reduces detection risks.
Also read | Critical WordPress Plugin Vulnerability Exposes Over 4 Million Sites
Key Features
- Hidden VNC and overlay attack techniques for stealing sensitive data.
- Keylogging and user interface monitoring to track user activities.
- Dual-channel communication for better operational efficiency.
- Disguised as legitimate apps to deceive users.
Origins of DroidBot
The threat actors behind DroidBot remain unknown. However, analysis of the malware suggests they are Turkish speakers.
Researchers noted that DroidBot is similar to other malware but stands out due to its operational model. The MaaS model is not commonly seen in such threats, making DroidBot a significant concern.
How to prevent this Attack
Users and organizations must stay vigilant to protect against DroidBot. Avoid downloading apps from unknown sources and check app permissions. Always update your devices with the latest security patches.
Banks and financial institutions should implement robust security measures to detect and prevent this type of malware.
Also read | Top 10 everyday apps that put your data at risk in 2024
DroidBot represents a new era of Android malware with its MaaS model and advanced techniques. It targets banks, cryptocurrency exchanges, and organizations, posing a significant security threat.
Users and businesses must take proactive steps to defend against DroidBot. Awareness and updated security practices are essential to minimize risks.
Found this article interesting? Follow us on Twitter and LinkedIn for more updates!

