The cybersecurity world was recently shaken by a ransomware attack that has everyone talking. The Qilin ransomware group, known for its sophisticated attacks, has now upped the ante by stealing credentials stored in Google Chrome browsers. This particular attack has only affected a small number of systems so far, but the implications are enormous, especially for those who rely on VPNs without multi-factor authentication (MFA) as their primary security measure.
What Makes This Attack Different?
Unlike traditional ransomware attacks that simply encrypt files and demand a ransom, the Qilin group took a more sinister approach. After gaining access to a target network using compromised VPN credentials, they bided their time. A full 18 days passed before they made their move, but when they did, the consequences were severe.
By reaching the domain controller, the attackers altered the default domain policy, adding a Group Policy Object (GPO) that included two scripts. The first, a PowerShell script named “IPScanner.ps1,” was designed to steal credential data stored in Chrome. The second, a batch script named “logon.bat,” ensured that the PowerShell script ran every time a user logged into their device.
For three long days, this malicious GPO was left active on the network. During this time, every time a user logged into their system, they unknowingly triggered the credential-harvesting script. Attackers continuously collect sensitive information with every logon, creating a treasure trove of stolen credentials for future attacks.
Qilin Ransomware: What Happens Next?
The stolen credentials were not the end of the Qilin group’s activities. After exfiltrating this valuable information, the attackers erased any evidence of their actions. They then proceeded to encrypt files across the compromised systems and dropped a ransom note in every directory. This double-edged approach, combining credential theft with ransomware, marks a dangerous evolution in cybercrime tactics.
For those unfortunate enough to be affected, the consequences are far-reaching. Victims now face the daunting task of changing usernames and passwords for every third-party site where they used their stolen credentials. This attack serves as a grim reminder that cybercriminals are constantly evolving their techniques to maximize their impact.
Also read | Microsoft to host cybersecurity summit after CrowdStrike-induced IT outage
Ransomware Trends in 2024
This Qilin ransomware attack is not an isolated incident. In 2024, ransomware groups actively refined their strategies, with other groups like Mad Liberator and Mimic making headlines.
The Mad Liberator group, for example, has been tricking victims with a fake Windows Update screen while secretly stealing data. These attackers use legitimate tools like remote desktop software to blend into regular network traffic, challenging cybersecurity teams immensely.
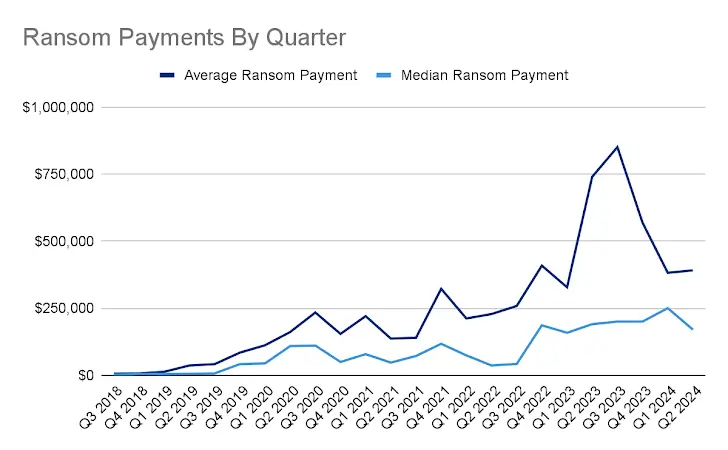
Despite law enforcement efforts to curb ransomware, the profitability of these attacks continues to soar. Ransomware payments soared to record highs in 2024, with the Dark Angels group securing a staggering $75 million ransom.
Also read | Gcore Report Reveals 46% Surge in DDoS Attacks in First Half of 2024
Ransomware Targets Critical Sectors
Ransomware attacks are increasingly targeting sectors where disruption would cause the most pain, such as industrials, consumer cyclicals, and hotels and entertainment. These industries are lucrative targets because their operations are mission-critical, and any downtime could have severe consequences.
Ransomware attacks on industrial organizations nearly doubled in one quarter of 2024, with North America suffering the most damage.
Qilin Ransomware in Cybercrime
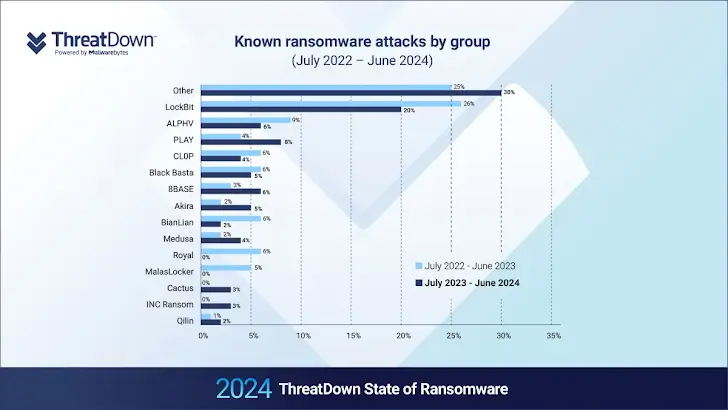
As we look to the future, it’s clear that ransomware groups will continue to adapt their tactics. A noticeable shift has been the increased exploitation of edge services and the targeting of small and medium-sized businesses. Moreover, the dismantling of major ransomware groups like LockBit and ALPHV has led to a rise in unaffiliated “lone wolf” attackers who operate independently, further complicating the cybersecurity landscape.
Continued takedowns of cybercriminal forums and marketplaces by law enforcement have shortened the lifespan of these sites, making it harder for attackers to operate. However, this also means that the cybercrime community is becoming more decentralized and unpredictable.

