Cybersecurity researchers have revealed a more dangerous variant of the Android banking trojan TrickMo. This trojan, designed to steal banking credentials, uses advanced tactics to evade detection. Let’s dive into how this tricky malware works and what makes it such a threat to your financial safety.
Key Takeaways:
- TrickMo is an Android trojan that steals banking credentials through advanced anti-analysis tactics.
- It exploits Android’s accessibility services to take full control of infected devices, performing on-device fraud.
- TrickMo can intercept SMS messages, record keystrokes, and overlay fake login screens.
- A recent security flaw in its C2 server exposed 12 GB of stolen data, putting victims at risk of identity theft and fraud.
- Always be cautious when enabling accessibility services and avoid downloading apps from untrusted sources.
A Sneaky Malware with New Tricks
The newly uncovered version of TrickMo doesn’t just steal passwords. It hides in plain sight using malformed ZIP files combined with JSONPacker to confuse analysts. When installed through a dropper app, it activates sophisticated anti-analysis mechanisms, making it harder for cybersecurity experts to catch and block it. This is no ordinary malware—it’s built to outsmart the system.
How TrickMo Targets Android Devices and Users
TrickMo first surfaced back in 2019, when it was used primarily against Android users in Germany. It cleverly intercepts one-time passwords (OTPs) and two-factor authentication (2FA) codes that banks often use to verify transactions. Over time, this malware has only gotten more dangerous, improving its ability to hide and evade detection.
The mobile-focused malware is thought to have been developed by the now-defunct TrickBot e-crime group. Its goal? Siphon your financial data while staying under the radar.
TrickMo Can Take Full Control of Your Device
One of the scariest things about TrickMo is how it manipulates Android’s accessibility services. This system is meant to help users with disabilities, but TrickMo exploits it to perform fraudulent actions on your device. It can record your screen, log your keystrokes, and even collect photos and SMS messages. If that isn’t enough, it can remotely control your device to commit on-device fraud (ODF).
By abusing accessibility services, TrickMo can overlay fake login screens on top of legitimate apps, tricking you into entering your credentials. It can also click and gesture on your screen without your knowledge.
Also read | Chameleon Android Banking Trojan Targets Users Through Fake CRM App
How TrickMo Infects Devices
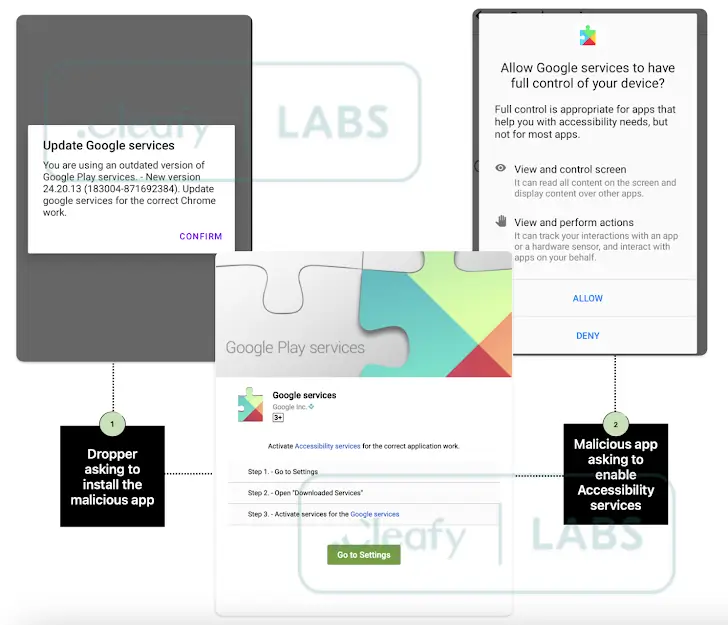
The malware disguises itself as a Google Chrome update, making it harder to spot. Once installed, it prompts users to update their Google Play Services by clicking a button. But instead of a real update, this triggers the download of an APK file containing the TrickMo trojan.
The real danger begins when TrickMo convinces you to enable accessibility services for the fake app. From that moment, the malware gains full control of your device, intercepting SMS messages, handling notifications, and even dismissing security updates.
Why TrickMo’s Accessibility Exploit Is So Dangerous
Accessibility services provide TrickMo with the power to auto-grant permissions, disable security features, and prevent the uninstallation of specific apps. This makes it nearly impossible for users to remove the malware without professional help. Once TrickMo takes over, it can intercept your two-factor authentication codes, allowing the attackers to bypass critical security layers for banking apps.
TrickMo Command-and-Control (C2) Server Leak
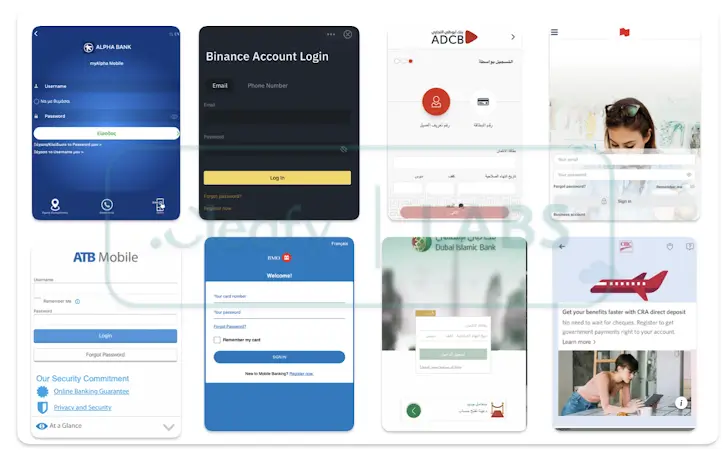
Cleafy’s cybersecurity experts recently discovered a vulnerability in TrickMo’s command-and-control (C2) server. This slip-up allowed researchers to access 12 GB of sensitive data stolen from infected devices. This included passwords, photos, and even banking credentials. The C2 server also hosted fake login pages for banks like ATB Mobile and cryptocurrency platforms like Binance.
This security lapse doesn’t just hurt the hackers. It also endangers victims, whose data could fall into the hands of other cybercriminals, leading to identity theft or financial fraud.
The Fallout from TrickMo’s Data Breach
With so much personal information exposed, the risk goes far beyond stolen passwords. Attackers can use the stolen data to lock victims out of their accounts, perform unauthorized transactions, or even reset account passwords. Worse yet, they could craft convincing phishing messages to trick users into revealing even more personal data.
This breach can cause immediate financial harm and long-term damage to your reputation and credit score. Recovering from such an attack can take months if not years.
How to Stay Safe from Android Banking Trojans Like TrickMo
TrickMo is a powerful reminder of how dangerous Android malware can be, especially when it uses accessibility services to execute its attacks. Always be cautious when downloading apps, and never enable accessibility services unless you trust the source. Google has been working hard to plug security holes in Android, but it’s still up to users to stay vigilant.
By keeping your software up to date and avoiding suspicious apps, you can reduce your chances of falling victim to tricky malware like TrickMo.

