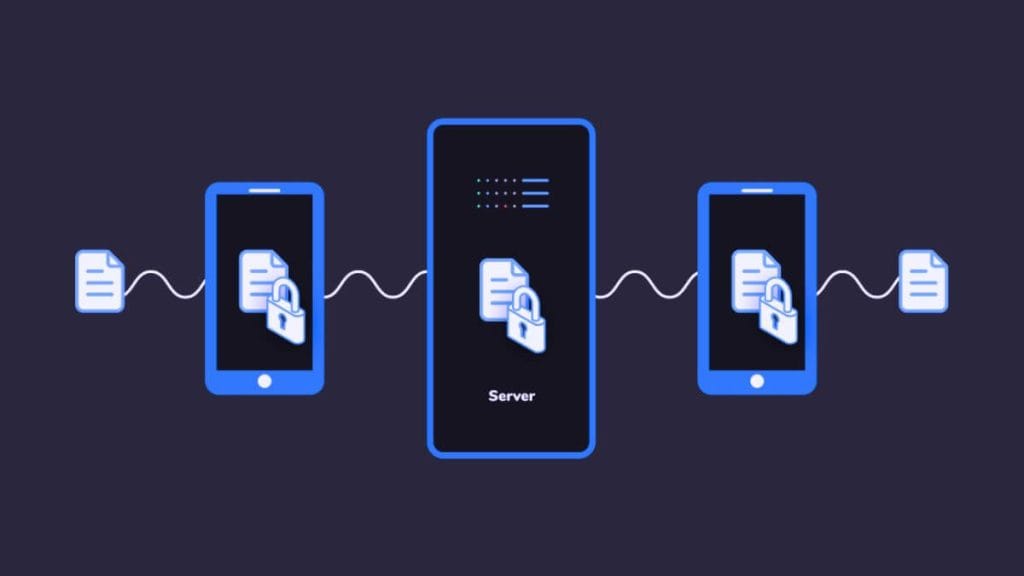
Information is a valuable asset, and encryption is one of the most effective ways to safeguard it. End-to-end (E2E) encryption is a powerful security mechanism that has revolutionized the approach of human rights organizations, law enforcement agencies, and technology companies toward accessing and utilizing information about individuals for various purposes such as protection, prosecution, or profit.
What is encryption?
Encryption is a process of converting plaintext or readable data into an unreadable format, known as ciphertext, using an algorithm and a cryptographic key. The purpose of encryption is to ensure that only authorized parties can access and understand the original data. This transformation makes it extremely difficult for unauthorized individuals or hackers to interpret the information, even if they manage to intercept it.
How Encryption Works:
Plaintext and Ciphertext: Plaintext is the original, readable data that you want to protect, such as a message or a file. Ciphertext is an encrypted form of plaintext, which appears as a random and unreadable sequence of characters.
Encryption Algorithm: An encryption algorithm is a mathematical formula used to transform plaintext into ciphertext. The strength of an encryption system often relies on the complexity of the algorithm.
Encryption Key: The encryption key is a unique piece of information that is used alongside the algorithm to encrypt and decrypt data. The key can be a string of characters or a complex mathematical value.
Public and Private Keys (Asymmetric Encryption): In some encryption systems, there are two keys: a public key for encryption and a private key for decryption. Public keys can be shared openly, while private keys are kept secret. This method is often referred to as asymmetric encryption.
Types of Encryption
Symmetric Encryption: In symmetric encryption, the same key is used for both encryption and decryption. This means that the sender and the recipient must both have the same key.
Asymmetric Encryption: As mentioned earlier, asymmetric encryption uses a pair of keys – a public key for encryption and a private key for decryption. This method is commonly used in secure communication channels.
End-to-End Encryption: It approach ensures that the data is encrypted on the sender’s device and can only be decrypted on the recipient’s device, making it highly secure even if the data passes through other servers.
What is E2E encryption?
End-to-end encryption (E2E Encryption) is a method of securing digital communication to prevent unauthorized access to sensitive information. Unlike traditional encryption methods, E2E encryption ensures that only the intended recipients can access and decipher the data. The “end-to-end” in its name refers to the fact that the encryption process occurs from the sender’s device to the recipient’s device, without any intermediaries having access to the unencrypted data.
There are two crucial forms of encryption in this setup: encryption-in-transit and end-to-end (E2E) encryption.
Encryption-in-transit refers to the process of encrypting a message before it is transmitted from the server to the user (or vice versa). This method is implemented to prevent unauthorized access to the message while it is being transmitted. On the other hand, End-to-End (E2E) encryption involves encrypting the message not only during transmission but also when it is stored on the server. The message is decrypted only when it is received by the intended recipient.
How Does E2E Encryption Work?
The fundamental principle behind E2E encryption is to transform the plaintext data into an unreadable format using a cryptographic key. This key is known only to the sender and the recipient, ensuring that even if the communication is intercepted, the data remains secure.
Key Generation: When a user initiates a conversation or sends a message, a unique cryptographic key pair is generated. This pair typically consists of a public key, known to everyone, and a private key, known only to the user.
Encryption: The sender’s message is encrypted using the recipient’s public key. This ensures that only the recipient, possessing the corresponding private key, can decrypt and read the message.
Transmission: The encrypted data is sent over the communication channel, be it text messages, emails, or any other form of digital communication.
Decryption: Upon receiving the encrypted message, the recipient uses their private key to decrypt and access the original content.
Why Does E2E Encryption Matter?
Data Privacy: E2E encryption is a powerful tool for safeguarding user privacy. It prevents service providers, hackers, or any other third parties from accessing the content of communications.
Security Against Interception: In an age where cyber threats are prevalent, E2E encryption protects against unauthorized interception of sensitive information during transmission.
Trust in Communication Services: With the rise of digital communication platforms, users are more conscious about the security of their conversations. E2E encryption builds trust by ensuring that only the intended recipients can access the information.
Compliance with Privacy Regulations: E2E encryption aligns with privacy regulations and standards, making it an essential element for services that handle sensitive user data.
What are hash functions?
A hash function is a mathematical algorithm that takes an input (or ‘message’) and produces a fixed-size string of characters, which is typically a hexadecimal number. The output, known as the hash value or hash code, is unique to each distinct input. It’s crucial to note that even a small change in the input should result in a significantly different hash value.
The hash function encrypts a message and is expected to have many properties.
- The function should take a message as input and generate a digest that does not reveal the original message.
- The hashing algorithm should be designed in such a way that it can handle messages of any length and produce a fixed-length digest, regardless of the original message’s length. This ensures that the length of the original message cannot be determined from the length of the digest.
- The hash function should produce unique digests for unique messages.
Common Uses of Hash Functions:
Password Storage: When you create an account on a website, your password isn’t stored directly; instead, its hash value is stored. During login attempts, the system hashes the entered password and compares it to the stored hash for authentication.
Data Integrity: Hash functions are employed to ensure the integrity of data during transmission or storage. By comparing the hash value of the original data with the received or stored hash value, one can verify if the data has been altered.
Cryptographic Applications: Hash functions are integral to various cryptographic protocols, such as digital signatures and blockchain technology. They provide a secure and efficient way to verify the authenticity and integrity of digital information.
Can End-to-End Encryption Be ‘Cracked’?
End-to-end encryption is a security measure that ensures only the sender and intended recipient of a message can access its content. This is achieved by encrypting the data on the sender’s device and decrypting it on the recipient’s device, with the encryption keys known only to the two parties involved. The idea is to create a secure communication channel that prevents unauthorized access, even if the data traverses through potentially insecure networks.
Theoretically, E2E encryption is designed to be uncrackable. The encryption algorithms employed are typically based on complex mathematical principles that make it computationally infeasible for anyone, including malicious actors or even the service providers facilitating the communication, to decipher the encrypted data without the correct decryption keys.
However, like any security measure, the effectiveness of E2E encryption relies heavily on its implementation. Vulnerabilities can arise from flaws in the encryption algorithms, improper key management, or weaknesses in the overall security infrastructure. In the past, there have been instances where vulnerabilities, such as the infamous Heartbleed bug, have exposed weaknesses in widely used encryption protocols, leading to concerns about the robustness of E2E encryption.
Another potential weak point is the endpoint devices themselves. If an attacker gains access to either the sender’s or recipient’s device, they may be able to bypass the encryption altogether. This is why users must maintain the security of their devices through practices like regular software updates, strong passwords, and device authentication measures.
In conclusion, while end-to-end encryption is a powerful tool for securing online communications, its effectiveness depends on proper implementation, ongoing security measures, and adaptability to emerging technological challenges. As of now, E2E encryption remains a formidable defense against unauthorized access, but continuous vigilance, research, and advancements are necessary to stay ahead of potential threats in the ever-evolving landscape of cybersecurity.