A critical vulnerability in a popular WordPress plugin has shocked website owners. The plugin, Really Simple Security, has over 4 million installations. Hackers can exploit this flaw to take control of websites.
The vulnerability is tracked as CVE-2024-10924. Its CVSS score of 9.8 shows it is highly dangerous. Both free and premium versions of the plugin are affected.
What Is the Vulnerability?
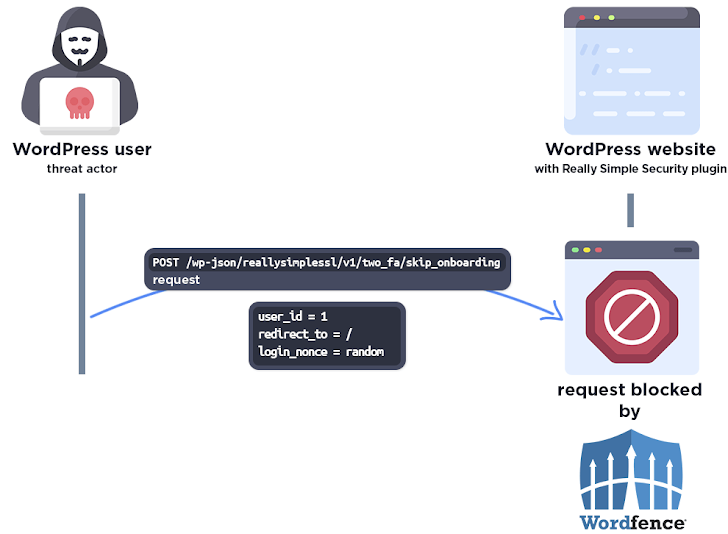
The issue lies in the plugin’s two-factor authentication feature. A function called “check_login_and_get_user” has a critical flaw. It fails to handle user verification correctly.
Hackers can use this flaw to bypass authentication. They can log in as any user, including administrators. This happens even if two-factor authentication is enabled.
Who Found the Vulnerability in WordPress Plugin?
Wordfence researchers discovered this vulnerability. István Márton, a Wordfence expert, explained the risks. He said attackers could automate the attack to target many websites.
The vulnerability is scriptable. This means hackers can launch large-scale attacks without much effort.
The issue was responsibly disclosed on November 6, 2024. The plugin developers quickly released a patch. The fixed version, 9.1.2, became available a week later.
WordPress worked with the developers to force-update affected sites. This reduced the risk before the public disclosure.
Also read | 2M+ WordPress Sites Hit By Essential Addons For Elementor Vulnerability
What Are the Risks?
If hackers exploit this vulnerability, they can fully take over websites. They can:
- Delete or modify site content.
- Add malicious scripts to spread malware.
- Steal sensitive data like user credentials.
Website hijacking can lead to criminal activities. Attackers might use compromised sites to launch further cyberattacks.
Also read | What is a digital arrest? A new deepfake tool used by cybercriminals
WordPress Plugin Security Issues
This vulnerability follows another recent WordPress flaw. The WPLMS Learning Management System plugin had a critical issue.
Before version 4.963, the WPLMS plugin allowed attackers to read and delete files, including sensitive files like wp-config.php. Deleting this file forced the site into setup mode.
Attackers could then take over the site by connecting it to a malicious database.
How to Protect Your WordPress Site
Follow these steps to secure your site from these vulnerabilities:
- Update Plugins Regularly
Always keep plugins updated to their latest versions. Developers release patches to fix such issues. - Remove Unused Plugins
Unnecessary plugins can become a security risk. Remove any plugins you do not actively use. - Enable Security Features
Install reliable WordPress security plugins. Use firewalls and malware scanners to detect threats. - Regular Backups
Back up your website data regularly. This ensures you can restore it in case of an attack. - Monitor Your Site
Watch for unusual activities like unknown admin accounts or sudden traffic spikes. - Check File Permissions
Limit file permissions to protect sensitive files like wp-config.php.
Also read | Top 10 everyday apps that put your data at risk in 2024
Final Thoughts
WordPress vulnerabilities are a serious threat. This Really Simple Security plugin flaw put over 4 million sites at risk.
The issue was quickly patched, helping prevent widespread attacks. However, website owners must remain vigilant, and regular updates and security practices are essential.
Follow trusted cybersecurity blogs to stay informed. Protect your site and users from evolving threats.
Found this article interesting? Follow us on Twitter and LinkedIn for more updates!

