Cybercriminals are targeting Google Ads users in a sophisticated malvertising campaign. This attack aims to steal credentials and two-factor authentication (2FA) codes. Researchers have uncovered the details of this scheme, which affects both individuals and businesses using Google Ads.
The attack’s Objective
The primary goal of the attack is to steal advertiser accounts. Attackers impersonate Google Ads and redirect victims to fake login pages. Once credentials are stolen, they are misused to hijack accounts, run malicious ads, or sold to other cybercriminals. This activity has been ongoing since November 2024 and has alarmed many advertisers worldwide.
How the attack Operates
Attackers rely on fake ads that appear in Google search results. When users search for “Google Ads,” they encounter fraudulent ads. Clicking these ads leads to phishing pages hosted on Google Sites. These pages then redirect users to external phishing sites.
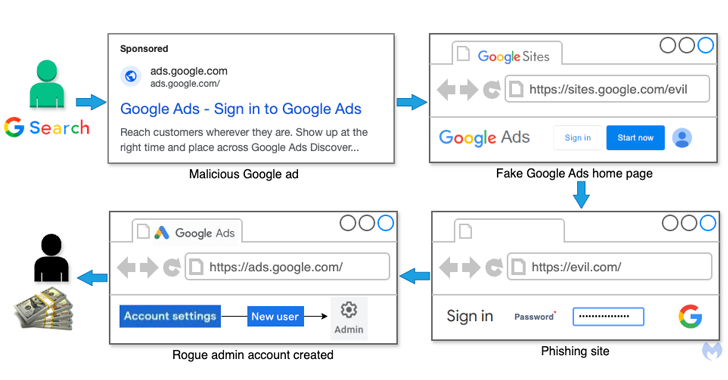
Source: malwarebytes.com
The phishing sites are cleverly designed to look like authentic Google login pages. They trick users into entering their credentials and 2FA codes. Once entered, the data is sent to a remote server controlled by the attackers.
Advanced Tactics Used by Attackers
The attack is successful due to advanced tactics. Attackers exploit a loophole in Google Ads, allowing the display URL to differ from the landing page. They host phishing pages on sites.google[.]com, while the displayed URL appears as ads.google[.]com. This makes the attack appear legitimate.
Techniques like fingerprinting, CAPTCHA-inspired lures, and cloaking further hide the phishing infrastructure. These tactics ensure the attack avoids detection by both users and security systems.
What Happens After Credentials Are Stolen?
Once attackers gain access to a Google Ads account, they add themselves as administrators. This gives them complete control over the account. They then use the victim’s advertising budget to run malicious ads. These ads attract more victims, creating a cycle of account takeovers.
The attackers also use stolen credentials to expand their campaigns. In many cases, these credentials are sold on underground forums to other cybercriminals. This adds to the scale of the attack and increases its impact.
Also read | Google OAuth Vulnerability Exposes Millions via Failed Startup Domains
Evidence Points to Portuguese-Speaking Groups
Researchers have identified that many attackers involved in this attack are Portuguese speakers. They operate from Brazil and use domains with the .pt extension. This regional clue helps trace the origins of the attack, but the global impact remains significant.
Google’s Response to the Attack
Google is aware of the issue and has taken measures to combat it. In 2023, Google removed over 3.4 billion ads and suspended 5.6 million advertiser accounts. These actions were part of their efforts to enforce ad policies and prevent abuse.
A Google spokesperson stated, “We prohibit ads that deceive users or steal information. Our teams are actively addressing this issue.” However, the scale and sophistication of the attack have made it challenging to eliminate completely.
Also read | AI-Powered Ransomware FunkSec Hits 85 Victims Globally
Other Related Cyber Threats
The malvertising attack is not an isolated incident. Researchers have also observed similar tactics on platforms like YouTube and SoundCloud. Attackers use these platforms to distribute links to fake software installers. These installers deploy malware like Amadey, Lumma Stealer, and Mars Stealer.
To evade detection, attackers use reputable file-hosting services like Mediafire and Mega.nz. Files are often password-protected and encoded, complicating their detection and analysis. This further highlights the growing sophistication of cybercriminal tactics.
Also read | Double Clickjacking: New “Double-Click” Attack to Hack Websites
Protecting Yourself from Malvertising Attacks
To stay safe from these attacks, users should follow these precautions:
- Verify the authenticity of Google Ads links before clicking.
- Avoid clicking on ads that look suspicious or unfamiliar.
- Enable two-factor authentication (2FA) but remain cautious of phishing attempts.
- Regularly monitor your Google Ads account for unauthorized activities.
- Use a reliable antivirus program to detect malicious activities.
Conclusion
The Google Ads malvertising attack is a serious threat to advertisers. By understanding its tactics and taking proactive measures, users can protect themselves. Cybersecurity awareness and vigilance remain the best defenses against such sophisticated attacks.

