Cybercriminals have stolen over 390,000 WordPress credentials using a malicious GitHub repository that posed as a legitimate WordPress tool. This attack targeted offensive actors, including pen testers and researchers, exposing sensitive data like SSH private keys and AWS access keys.
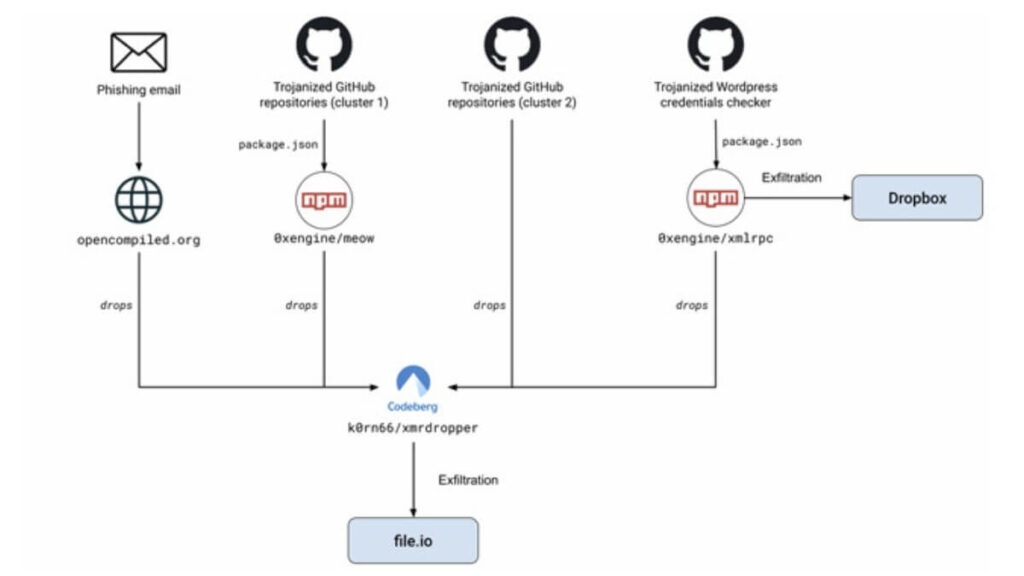
The cyberattack involved a malicious actor named MUT-1244. The group targeted victims using phishing emails and trojanized GitHub repositories. These repositories falsely claimed to host proof-of-concept (PoC) exploits for security flaws.
How attackers exploited GitHub repositories for WordPress credentials
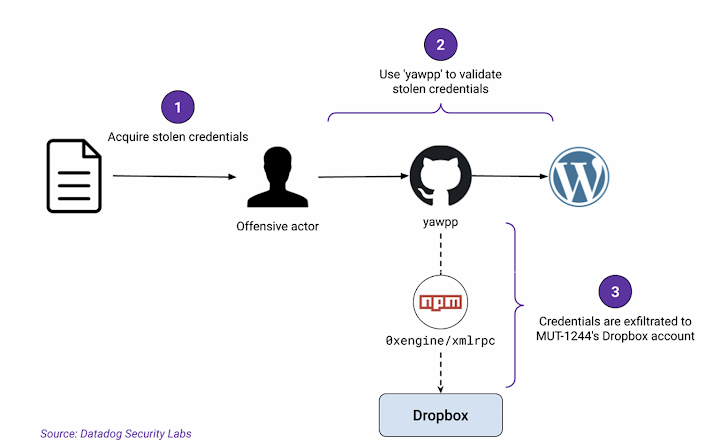
The attackers created fake GitHub repositories with phony profiles. These profiles appeared to offer tools and scripts for WordPress. One such repository, “github[.]com/hpc20235/yawpp,” claimed to be a tool for creating WordPress posts.
This tool contained two scripts. One script validated WordPress credentials, and the other used XML-RPC API to publish posts. However, the scripts also contained malicious code. This code used a rogue npm dependency named “@0xengine/xmlrpc” to deliver malware.
Malware delivery through fake tools
The malware was designed to steal system information and sensitive data. This included SSH keys, AWS credentials, and environmental variables. The malware also uploaded stolen credentials to an attacker-controlled Dropbox account.
Cybersecurity firm Checkmarx found that the npm package “@0xengine/xmlrpc” remained active for over a year. During this time, it was downloaded approximately 1,790 times.
Phishing emails as another attack vector
The attackers also used phishing emails to target academics. Victims were tricked into copying and pasting shell commands into their terminal. These commands claimed to upgrade the kernel but instead deployed malware.
This marked the first-ever ClickFix-style attack on Linux systems. The phishing emails and GitHub repositories worked together to deliver the second-stage payload.
Also read | Hackers using fake video apps to target Web3 Professionals data
Impact on victims
MUT-1244’s campaign compromised the systems of dozens of victims. Most victims were red teamers, security researchers, and those downloading PoC exploit code. Attackers gained access to SSH private keys, AWS credentials, and command history from compromised systems.
The stolen credentials were used to further compromise WordPress accounts. Researchers believe many credentials belonged to unrelated threat actors who accessed them illegally.
Techniques used by MUT-1244
MUT-1244 deployed the malware in multiple ways:
- Backdoored configuration files.
- Malicious payloads in PDF files.
- Python-based droppers.
- Malicious npm packages like “0xengine/meow.”
Each method was carefully designed to evade detection and steal maximum data.
How fake GitHub repositories target victims for WordPress credentials
MUT-1244 hosted fake GitHub repositories that looked convincing. They used AI-generated profile pictures and appeared professional. MUT-1244 created most repositories in late 2024, targeting researchers and pen-testers.
Cybersecurity experts previously highlighted these repositories. However, MUT-1244 continued to exploit them to distribute malware.
Also read | Malicious Chrome VPN Extensions Installed 1.5 Million Times
Broader trends in cyberattacks
In recent years, cybercriminals have exploited vulnerability disclosures to create fake PoC repositories. These repositories not only steal data but also demand payments for exploits.
Nation-state groups from countries like North Korea have targeted researchers. They aim to steal information about undisclosed security vulnerabilities. This information can help launch further attacks.
Also read | What is a digital arrest? A new deepfake tool used by cybercriminals
Steps to avoid WordPress credentials attacks:
Users should verify the source of GitHub repositories before downloading any code. They should check for legitimate activity in the repository’s history and avoid downloading tools from unknown or unverified developers.
Phishing emails should always be handled with caution. Do not execute commands or download files from unverified emails.
Conclusion
MUT-1244 launched the attack, serving as a wake-up call for the cybersecurity community. A malicious GitHub repository exposed over 390,000 WordPress credentials.
The incident highlights the growing threat posed by fake PoC repositories and phishing attacks. Security researchers and offensive actors must remain vigilant to avoid such traps.
Staying updated on cybersecurity news and adopting best practices can minimize risks. Always validate the authenticity of tools and repositories. Cybersecurity awareness is the key to staying protected in today’s digital landscape.