Switching to a new Android device often means dealing with login issues for apps. Google’s Restore Credentials tool simplifies app logins after Android migration, offering seamless and secure account access.
Google aims to fix this by restoring credentials. This new feature simplifies account restoration for third-party apps during Android migration. It ensures secure and hassle-free access to your apps without re-entering credentials.
What Is Restore Credentials?
Restore Credentials is a feature introduced as part of Android’s Credential Manager API. It eliminates the need for manually entering login details after switching devices. This tool securely restores app logins when users move to a new Android device.
The feature operates seamlessly in the background. It uses a secure restore key to sign users into apps automatically. This ensures users can access their accounts without any additional steps.
How to Restore Credentials Works
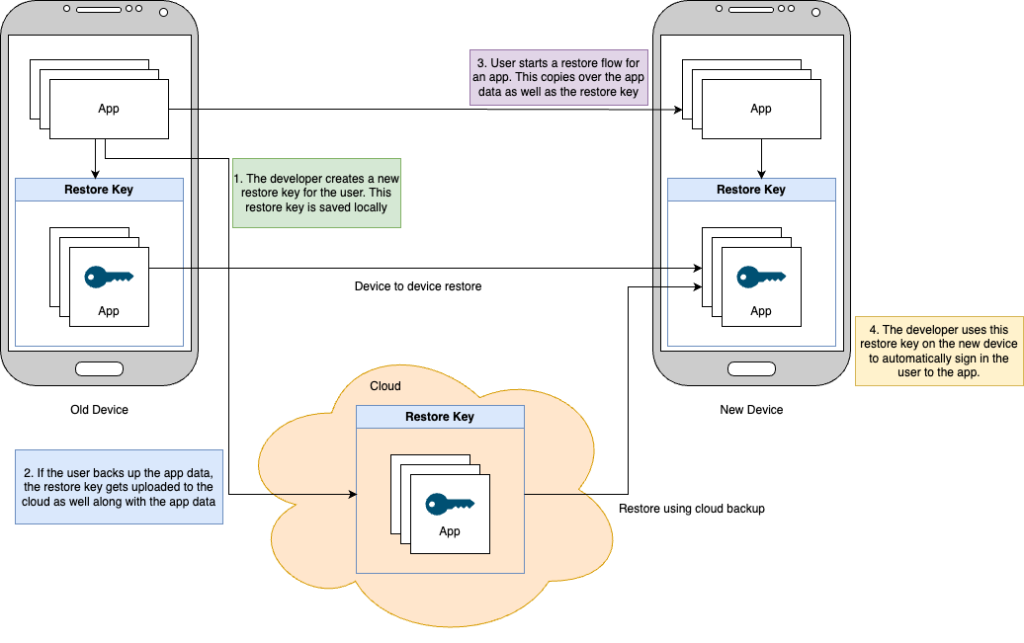
When you log in to an app supporting this feature, it generates a restore key. This restore key is a public key compatible with FIDO2 standards like passkeys. It is saved securely in two ways. First, it is stored locally on the device in an encrypted format. Second, if cloud backup is enabled, it is encrypted and stored in the cloud.
When you migrate to a new Android device, the restore key is automatically retrieved. This allows the app to log you in without asking for credentials. The process ensures smooth account restoration during migration.
Google allows developers to control when the restore key is generated. Developers can create this key right after a user logs into the app. Alternatively, they can generate it during periodic security checks within the app.
If a user logs out of the app, developers are advised to delete the restore key. This prevents unwanted login loops.
Also read | Critical WordPress Plugin Vulnerability Exposes Over 4 Million Sites
Benefits of Restore Credentials for Users
This feature offers several benefits to users.
It removes the frustration of entering credentials after switching phones. Users no longer need to remember multiple passwords. The tool saves time by restoring logins automatically during the migration process.
Security is another key benefit. The restore key is encrypted and stored securely, ensuring user data is safe from breaches.
How Restore Credentials Enhances the Android Experience
Restore Credentials makes Android migration simpler and more user-friendly. The feature eliminates one of the most tedious aspects of moving to a new device.
Users can now set up their new phones faster. They no longer need to spend time entering login details for every app. This improved experience aligns with Google’s efforts to enhance Android usability.
The feature also integrates well with other Android tools, making it a valuable addition to the operating system.
For App Developers
Restore Credentials is not just beneficial for users; it is also important for developers.
Google provides guidelines for integrating this feature into apps. Developers can use the Credential Manager API to implement restore key functionality. This makes their apps more user-friendly and secure.
Apps that support this feature can attract more users. A smooth login process enhances user satisfaction. Developers also gain the ability to control key generation and deletion. This flexibility helps them manage security better.
Comparison with Apple’s iCloud Keychain
Apple offers a similar feature for iOS through iCloud Keychain. It uses an attribute called kSecAttrAccessible to manage app credentials.
This attribute lets developers control credential access based on the device’s lock state. It also determines whether credentials can migrate to a new device. Credentials with the ThisDeviceOnly string cannot be restored to another device. This ensures added privacy for users.
Google’s Restore Credentials, on the other hand, uses encrypted restore keys. These keys work across devices if cloud backup is enabled. This approach focuses on making app logins seamless during migration.
While both features aim to simplify account restoration, they differ in execution and scope.
Part of Android’s Broader Security Updates
Restore Credentials is part of Google’s ongoing efforts to enhance Android security and usability.
The feature was introduced alongside the Android 16 Developer Preview. This preview includes updates to the Privacy Sandbox and Privacy Dashboard.
The Privacy Sandbox improves user privacy by limiting data sharing across apps. The updated Privacy Dashboard lets users view which apps accessed sensitive permissions over the last seven days.
Google also released an updated Android Security Paper. This document outlines the operating system’s built-in security features. These include theft protection, private space, and sanitizers. Another notable feature is lockdown mode, which enhances device security during emergencies.
Also read | What is a digital arrest? A new deepfake tool used by cybercriminals
How to Use Restore Credentials
For users, the process is simple. Enable cloud backup on your current Android device. During migration, restore apps and data from the cloud. If an app supports Restore Credentials, your login details will be restored automatically.
For developers, Google provides detailed instructions to implement this feature. Developers need to integrate the Credential Manager API into their apps. They can then generate restore keys securely and delete them when users log out.
Why This Feature Matters
Restore Credentials addresses a common pain point for Android users. Migrating to a new device is now faster and easier, and users no longer need to deal with the frustration of manual logins.
This feature also showcases Google’s commitment to improving the Android ecosystem. It balances usability and security, providing a better experience for both users and developers.
Also read | How Do AI Detectors Work?
Conclusion
Google’s Restore Credentials tool simplifies app logins after Android migration. It enhances user experience by automating the login process. The tool uses secure encryption, ensuring data safety.
For users, it saves time and reduces stress during device migration. For developers, it offers flexibility and improves app appeal. This feature is a step forward in making Android more user-friendly.
Found this article interesting? Follow us on Twitter and LinkedIn for more updates!

